Methodology of Code Review
Code review is a systematic task that requires us to identify security vulnerabilities in existing code. We need to build a model that can be used to guide the proccess of code reviewing.
Below are some of my thoughts.
- Network protocol
- Sensitive information leak: include hard code credentials, public-private key, IP, URL and source code etc.
- Risk of configuration
- Risk of Component
-
Vulnerabilities of code
- Broken Access Control
- Injection
- etc
Learn Basic of ASP.NET
Learn from video is the fast way to improve you operation skill.
Official Document
Build a sample application
Create new web application in vs.

The visual studio will automatically create a Web Form website

It cann be noticed that an aspx file is actually composed of two parts, the front-end .aspx file and the back-end .cs file.
The “CodeFile” specified in the front-end .aspx file refers to the corresponding .cs file.

All of .cs file are inherit from the Page class.


Empty web application
Ceate a empty website
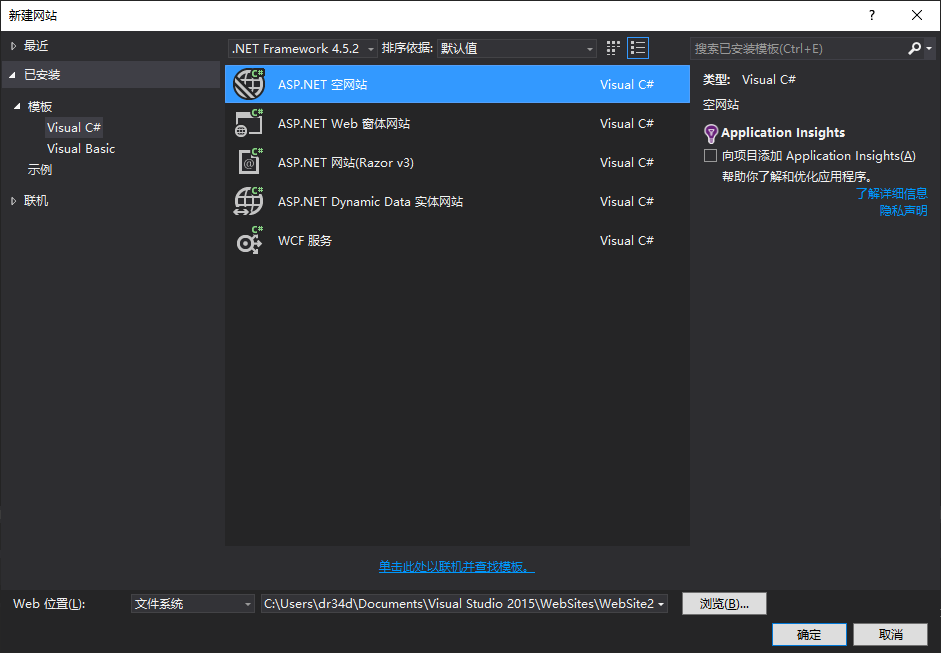
Creat a Web Form
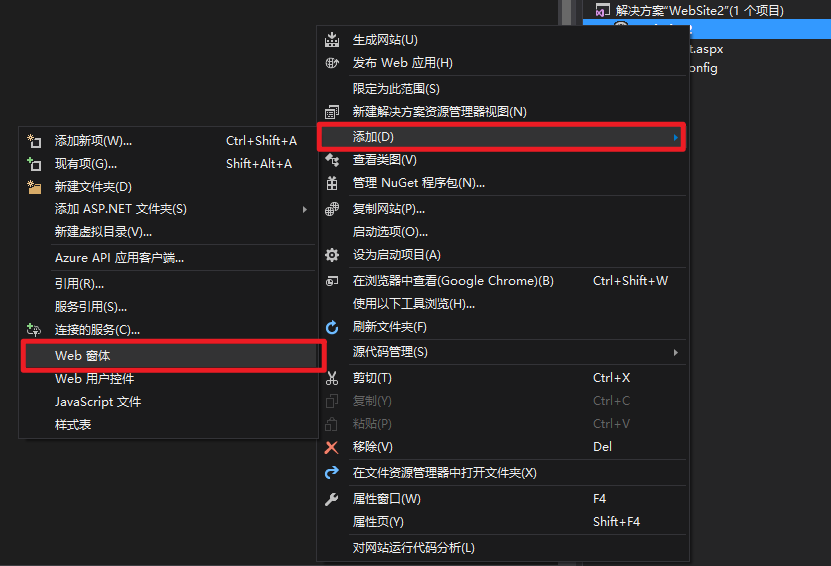
This will generate an aspx file.

点击下方的拆分可以同时看到 aspx 前端源码以及设计界面。
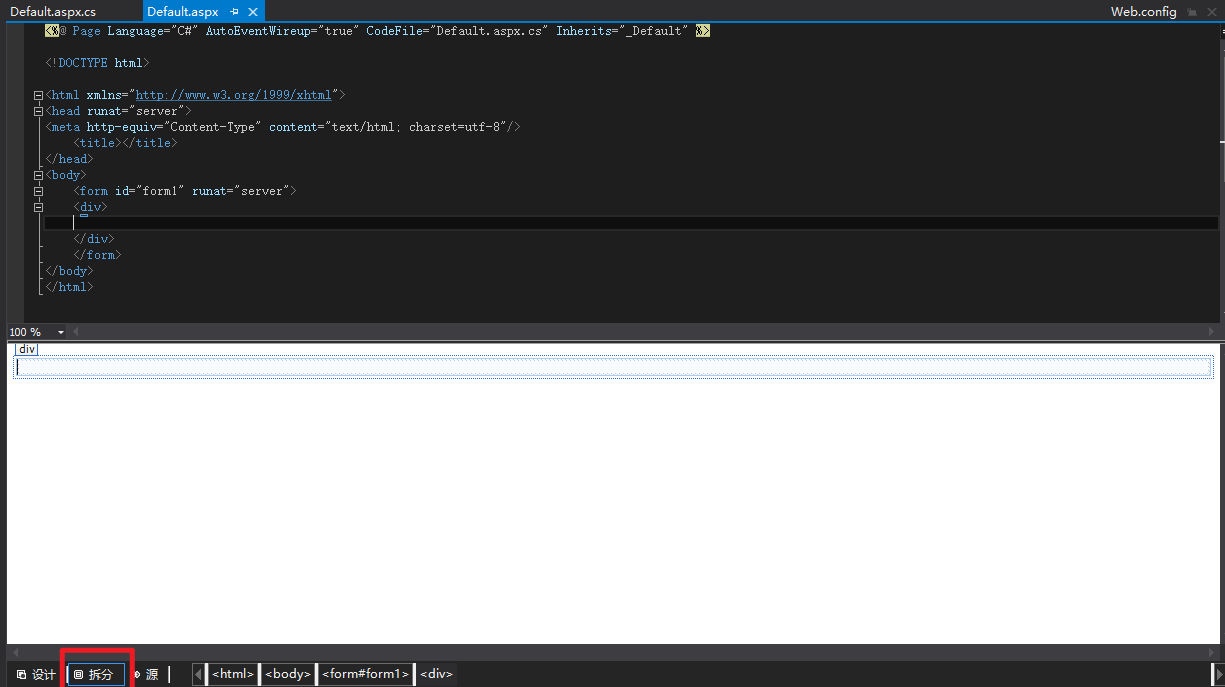
Open the tool box
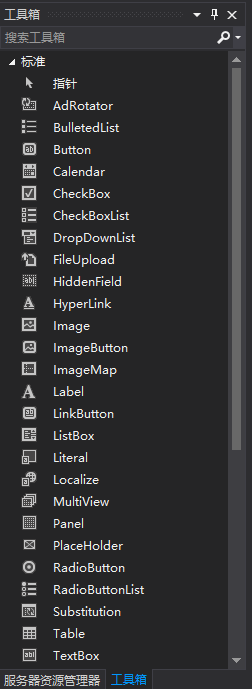
We can drag corresponding controls from the toolbox onto the design surface. Here is an TextBox and I modifyied its ID in the properties page.
Other controls are the same, such as the button below.
So as the following label.

Double-clicking on a control in the design surface will take you to the code editor. The btnSure_Clickis the function that is executed when the button is click.

We can code whatever within this function.
Build Environment
ASP.NET Environment
SQL Server
Tools
SAST tools
Fortify SCA
Fortify Static Code Analyzer (SCA) is a software security tool that is used to identify and fix vulnerabilities in software applications. It is designed to analyze the source code of an application and identify potential security flaws before the application is deployed. Fortify SCA provides developers with a comprehensive security analysis of their code, including identifying vulnerabilities, providing remediation guidance, and tracking progress over time. This helps organizations to build more secure applications and reduce the risk of security breaches.
Download links:
version 22.1
链接:https://pan.baidu.com/s/1K5QdQJCjzeW5_MVfcPR45g?pwd=4j0u
提取码:4j0u
–来自百度网盘超级会员V5的分享
version 20.1.1
链接:https://pan.baidu.com/s/1jleP1gfHUfkqer2kAULYnA?pwd=wcmt
提取码:wcmt
–来自百度网盘超级会员V5的分享
解压密码:shungg.cn
dnSpy
dnSpy is a free and open-source .NET debugger and assembly editor. It is used by developers and security researchers to reverse engineer .NET applications and analyze their code. dnSpy can decompile .NET assmblies into C#,Visual Basic and IL code, allowing users to view and modify the code of an application. It also includes a debugger that allow users to stop through the code of an application, set breakpoints, and inpsect variables.
dnSpy supports a wide range of .NET assemblies, including .NET core, .NET Standard, and .NET Framework.
Download link:
- https://github.com/dnSpy/dnSpy
dotPeek
dotPeek is a free and lightweight .NET decompiler and code viewer developed by JetBrains. It is used by developers and software engineers to reverse engineer .NET applications and view their source code. dotPeek can decompile .NET assemblies into C#, VB.NET, and IL code, allowing users to easily view and analyze the code of an application.
Download link:
- https://www.jetbrains.com/decompiler/download/
Both dotPeek and dnSpy are .NET decompilers and code viewers, but they have some differences in terms of features and capabilities.
dotPeek is a lightweight and user-friendly tool that is well-suited for viewing and analyzing code, while dnSpy is a more advanced tool that includes a debugger and is better suited for reverse engineering and modifying code.
Front-end code viewing tool.
Visual Studio
Visual Studio provides a range of features and tools that make ASP.NET development easier and more efficient.
- Visual Design: Visual Studio includes a visual design tool that allows developers to create ASP.NET web pages using drag-and-drop controls. This helps developers create visually appealing and responsive web pages quickly.
In the work of code review, we often face the dilemma of having only .aspx files and binary files. Visual Studio can display front-end pages with only .aspx files, which is very helpful for our auditing of front-end forms and input parameters.
It is recommended to use Visual Studio 2015 or later versions as they can intergrate better with Fortify SCA.
Third part component check
DependencyCheck
Download link:DependencyCheck**
Environment required:
To analyze .NET Assemblies the dotnet 6 run time or SDK must be installed.
- Assemblies targeting other run times can be analyzed - but 6 is required to run the analysis.
Usgae:
On *nix
$ ./bin/dependency-check.sh -h
$ ./bin/dependency-check.sh --out . --scan [path to jar files to be scanned]
On Windows
> .\bin\dependency-check.bat -h
> .\bin\dependency-check.bat --out . --scan [path to jar files to be scanned]
On Mac with Homebrew Note - homebrew users upgrading from 5.x to 6.0.0 will need to run dependency-check.sh --purge.
$ brew update && brew install dependency-check
$ dependency-check -h
$ dependency-check --out . --scan [path to jar files to be scanned]
Other tools
C# Online
SonarSource
Security Code Scan
Installation
- Visual Studio extension. Use the link or open “Tools > Extensions and Updates…” Select “Online” in the tree on the left and search for SecurityCodeScan in the right upper field. Click “Download” and install.
-
- Right-click on the root item in your solution. Select “Manage NuGet Packages for Solution…”. Select “Browse” on the top and search for SecurityCodeScan.VS2019. Select project you want to install into and click “Install”.
- Another option is to install the package into all projects in a solution: use “Tools > NuGet Package Manager > Package Manager Console”. Run the command
Get-Project -All | Install-Package SecurityCodeScan.VS2019.
- Stand-alone runner. Install with
dotnet tool install --global security-scan and runsecurity-scan /your/solution.sln. For older .NET 4.x please usesecurity-scan4x.zip from GitHub Releases.
reko
ReSharper
Debug
dnSpy provides additional debugging functionality. When debugging .net framework projects, you need to drag the DLLs in the /bin directory into dnSpy. You can determine which DLLs are compiled from developer code, which are third-party libraries, and which are system libraries by observing the file names in the /bin directory.
Here is an example: filenames like App_Web_xxx and App_Code are developer-written code in .net framework projects, App_Code.dll comes from the App_Code directory in the source code, App_Web_xxx comes from other directories, and log4net.dll is a third-party library. DLLs starting with “System” are generally system libraries.
├── ADO.dll
├── AjaxControlToolkit.dll
├── AntiXSSLibrary.dll
├── Apmtech.dll
├── App_Browsers.dll
├── App_Code.dll
├── App_global.asax.dll
├── App_Web_0pk0kvkf.dll
├── App_Web_0xkl5pmw.dll
├── App_Web_d4msxdcz.dll
├── App_Web_elxhpigl.dll
├── App_Web_fyo2axmt.dll
├── App_Web_jgcwvu0c.dll
├── App_Web_kcgcewvf.dll
├── App_Web_liiehwei.dll
├── App_Web_lond3s1y.dll
├── App_Web_lqvh1efk.dll
├── App_Web_o24jbtmm.dll
├── App_Web_oovjeiib.dll
├── App_Web_r3tukein.dll
├── App_WebReferences.dll
├── App_Web_wcbicfv1.dll
├── App_Web_yjumwbb1.dll
├── App_Web_yqwe0f2h.dll
├── log4net.dll
├── System.Web.Helpers.dll
...
After dragging the dll into dnSpy, you can also identify the developer’s own code compiled in the .net framework project by version. The version of the developer’s own code is generally 0.0.0.0.
You can perform additional debugging of the .net framework in dnSpy by following these steps:
Debug –> Attach to Process –> w3wp.exe –> Attach
Cases where breakpoints are invalid
In some cases, breakpoints are set but appear to be invalid in dnSpy. This is often because the opened dll is not loaded into memory. The following steps can help resolve this issue:
- Search for the class you want to debug in the Search window. Once found, double-click to enter the code page for the class.
- Check the name of the dll where the class is located, such as App_Web_jgcwvu0c.dll.
- In the Modules window, search for this dll and double-click to open it. Often, the opened dll is not the one you previously dragged into dnSpy. This newly opened dll is the one that has actually been loaded into memory.
- Locate the section you want to debug in the newly opened dll, set breakpoints, and attach to debug again.
Decompile
You can drag all the dlls to be decompiled into dnSpy, then select all –> Export to Project.
You can also use the dnSpy terminal program to decompile in batches. Place the dlls to be decompiled in a directory, and use dnSpy.Console.exe -o C:\out\path C:\some\path to decompile them.
Vulnerabilitis
Vulnerability Samples
Labs
- WebGoat.NET - OWASP WebGoat.NET
- Damn Vulnerable Thick Client App - DVTA is a Vulnerable Thick Client Application developed in C# .NET
- ASP.NET Vulnerable Site - Online .NET application that can be used to practice hacking.
Blogs
- 初识.Net审计
- 卷入.NET WEB
- 记一次靠猜的.net代码审计拿下目标
- Unable to trigger injection flaws for C# with Developer Edition
github repo